Postcard from Monterey 3 #CISmcc
Days 3 and 4 at CIS Monterey.
Andre Durand's Keynote
The main sessions at the Cloud Identity Summit (namely days three and four overall) kicked off with keynotes from Ping Identity chief Andre Durand, New Zealand technology commentator Ben Kepes, and Ping Technical Director Mark Diodati. I'd like to concentrate on Andre's speech for it was truly fresh.
Andre has an infectious enthusiasm for identity, and is a magnificent host to boot. As I recall, his CIS keynote last year in Napa was pretty simply a dedication to the industry he loves. Not that there's anything wrong with that. But this year he went a whole lot further, with a rich deep dive into some things we take for granted: identity tokens and the multitude of security domains that bound our daily lives.
It's famously been said that "identity is the new perimeter" and Andre says that view informs all they do at Ping. It's easy I think to read that slogan to mean security priorities (and careers) are moving from firewalls to IDAM, but the meaning runs deeper. Identity is meaningless without context, and each context has an edge that defines it. Identity is largely about boundaries, and closure.
MyPOV and as an aside: The move to "open" identities which has powered IDAM for a over a decade is subject to natural limits that arise precisely because identities are perimeters. All identities are closed in some way. My identity as an employee means nothing beyond the business activities of my employer; my identity as an American Express Cardholder has no currency at stores that don't accept Amex; my identity as a Qantas OneWorld frequent flyer gets me nowhere at United Airlines (nor very far at American, much to my surprise). We discovered years ago that PKI works well in closed communities like government, pharmaceutical supply chains and the GSM network, but that general purpose identity certificates are hopeless. So we would do well to appreciate that "open" cross-domain identity management is actually a special case and that closed IDAM systems are the general case.
Andre reviewed the amazing zoo of hardware tokens we use from day to day. He gave scores of examples, including driver licenses of course but license plates too; house key, car key, garage opener, office key; the insignias of soldiers and law enforcement officers; airline tickets, luggage tags and boarding passes; the stamps on the arms of nightclub patrons and the increasingly sophisticated bracelets of theme park customers; and tattoos. Especially vivid was Andre's account of how his little girl on arriving at CIS during the set-up was not much concerned with all the potential playthings but was utterly rapt to get her ID badge, for it made her "official".
Tokens indeed have always had talismanic powers.
Then we were given a fly-on-the-wall slide show of how Andre typically starts his day. By 7:30am he has accessed half a dozen token-controlled physical security zones, from his home and garage, through the road system, the car park, the office building, the elevator, the company offices and his own corner office. And he hasn't even logged into cyberspace yet! He left unsaid whether or not all these domains might be "federated".
MyPOV: Isn't it curious that we never seem to beg for 'Single Sign On' of our physical keys and spaces? I suspect we know instinctively that one-key-fits-all would be ridiculously expensive to retrofit and would require fantastical cooperation between physical property controllers. We only try to federate virtual domains because the most common "keys" - passwords - suck, and because we tend to underestimate the the cost of cooperation amongst digital RPs.

Tokens are, as Andre reminded us, on hand when you need them, easy to use, easy to revoke, and hard to steal (at least without being noticed). And they're non-promiscuous in respect of the personal information they disclose about their bearers. It's a wondrous set of properties, which we should perhaps be more conscious of in our work. And tokens can be used off-line.
MyPOV: The point about tokens working offline is paramount. It's a largely forgotten value. Andre's compelling take on tokens makes for a welcome contrast to the rarely questioned predominance of the cloud. Managing and resolving identity in the cloud complicates architectures, concentrates more of our personal data, and puts privacy at risk (for it's harder to unweave all the traditionally independent tracks of our lives).
In closing, Andre asked a rhetorical question which was probably forming in most attendees' minds: What is the ultimate token? His answer had a nice twist. I thought he'd say it's the mobile device. With so much value now remote, multi-factor cloud access control is crucial; the smart phone is the cloud control du jour and could easily become the paragon of tokens. But no, Andre considers that a group of IDAM standards could be the future "universal token" insofar as they beget interoperability and portability.
He said of the whole IDAM industry "together we are networking identity". That's a lovely sentiment and I would never wish to spoil Andre Durand's distinctive inclusion, but on that point technically he's wrong, for really we are networking attributes! More on that below and in my previous CISmcc diary notes.
The identity family tree
My own CISmcc talk came at the end of Day 4. I think it was well received; the tweet stream was certainly keen and picked up the points I most wanted to make. Attendance was great, for which I should probably thank Andre Durand, because he staged the Closing Beach Party straight afterwards.
I'll post an annotated copy of my slides shortly. In brief I presented my research on the evolution of digital identity. There are plenty of examples of how identity technologies and identification processes have improved over time, with steadily stronger processes, regulations and authenticators. It's fascinating too how industries adopt authentication features from one another. Internet banking for example took the one-time password fob from late 90's technology companies, and the Australian PKI de facto proof-of-identity rules were inspired by the standard "100 point check" mandated for account origination.
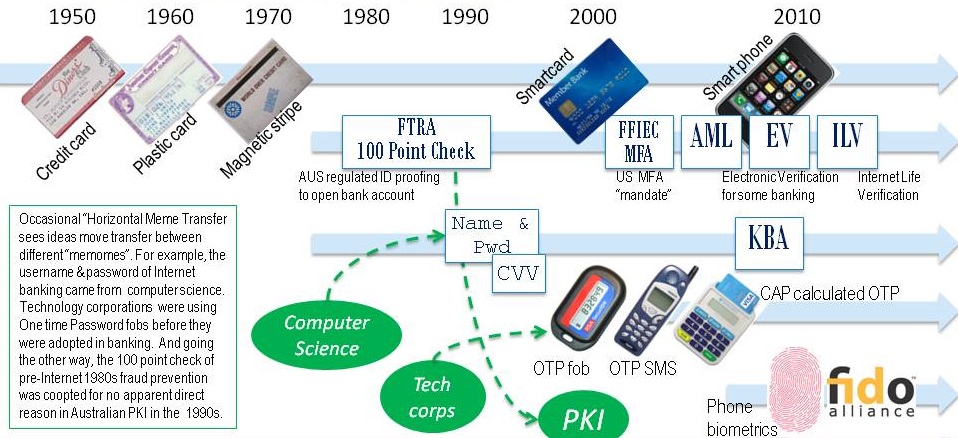
Clearly identity techniques shift continuously. What I want to do is systematise these shifts under a single unifying "phylogeny"; that is, a rigorously worked-out family tree. I once used the metaphor of a family tree in a training course to help people organise their thinking about authentication, but the inter-relationships between techniques was guesswork on my part. Now I'm curious if there is a real family tree that can explain the profusion of identities we have been working so long on simplifying, often to little avail.
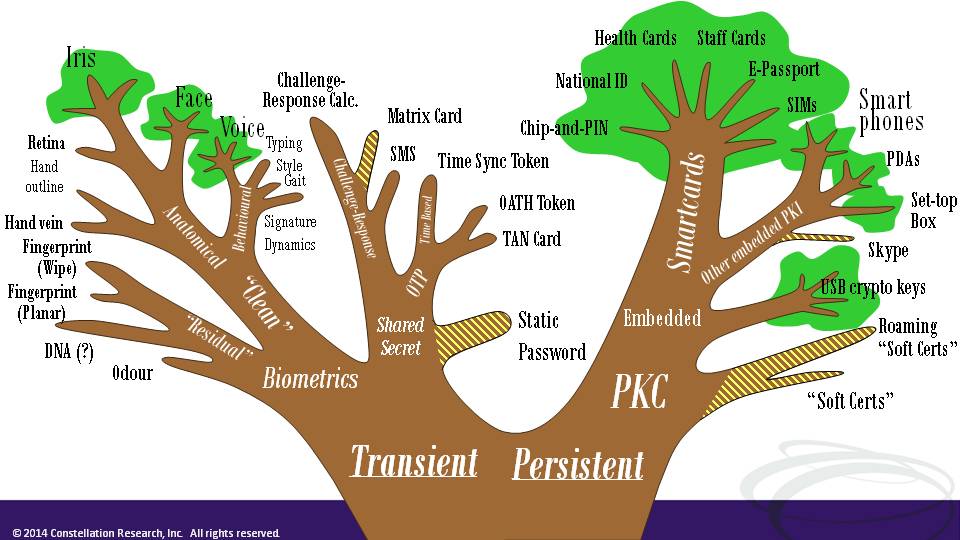
True Darwinian evolution requires there to be replicators that correspond to the heritable traits. Evolution results when the proportions of those replicators in the "gene pool" drift over generations as survival pressures in the environment filter beneficial traits. The definition of Digital Identity as a set of claims or attributes provides a starting point for a Darwinian treatment. I observe that identity attributes are like "Memes" - the inherited units of culture first proposed by biologist Richard Dawkins. In my research I am trying to define sets of available "characters" corresponding to technological, business and regulatory features of our diverse identities, and I'm experimenting with phylogenetic modelling programs to see what patterns emerge in sets of character traits shared by those identities.
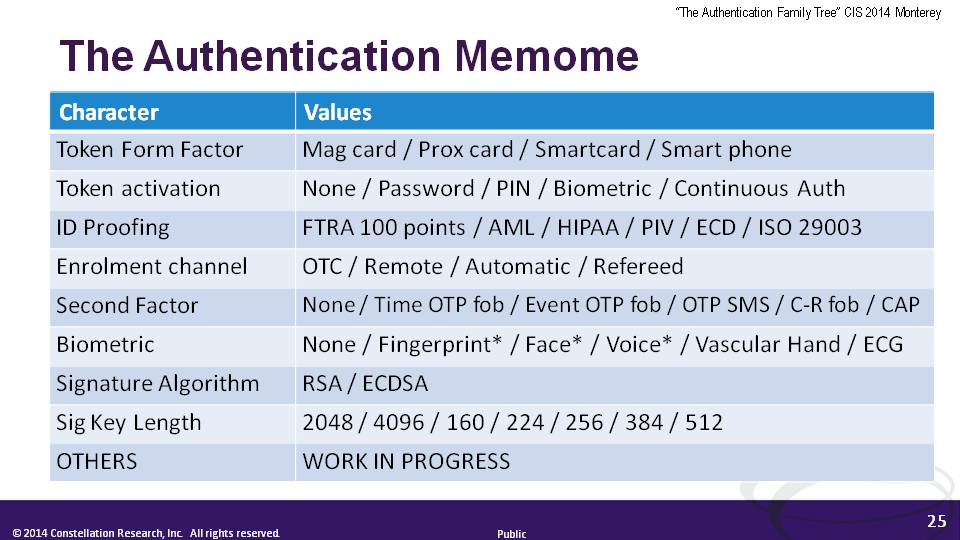
So what? A rigorous scientific model for identity evolution would have many benefits. First and foremost it would have explanatory power. I do not believe that as an industry we have a satisfactory explanation for the failure of such apparently good ideas as Information Cards. Nor for promising federation projects like the Australian banking sector's "Trust Centre" and "MAMBO" lifetime portable account number. I reckon we have been "over federating" identity; my hunch is that identities have evolved to fit particular niches in the business ecosystem to such an extent that taking a student ID for instance and using it to log on to a bank is like dropping a saltwater fish into a freshwater tank. A stronger understanding of how attributes are organically interrelated would help us better plan federated identity, and to even do "memetic engineering" of the attributes we really want to re-use between applications and contexts.
If a phylogenetic tree can be revealed, it would confirm the 'secret lives' of attributes and thereby lend more legitimacy to the Attributes Push (which coincidentally some of us first spotted at a previous CIS, in 2013). It would also provide evidence that identification risks in local environments are why identities have come to be the way they are. In turn, we could pay more respect to authentication's idiosyncrasies, instead of trying to pigeonhole them into four rigid Levels of Assurance. At Sunday's NSTIC session, CTO Paul Grassi floated the idea of getting rid of LOAs. That would be a bold move of course; it could be helped along by a new fresh focus to attributes. And of course we kept hearing throughout CIS Monterey about the FIDO Alliance with its devotion to authentication through verified device attributes, and its strategy to stay away from the abstract business of identities.
Reflections on CIS 2014
I spoke with many people at CIS about what makes this event so different. There's the wonderful family program of course, and the atmosphere that creates. And there's the paradoxical collegiality. Ping has always done a marvelous job of collaborating in various standards groups, and likewise with its conference, Ping's people work hard to create a professional, non-competitive environment. There are a few notable absentees of course but all the exhibitors and speakers I spoke to - including Ping's direct competitors - endorsed CIS as a safe and important place to participate in the identity community, and to do business.
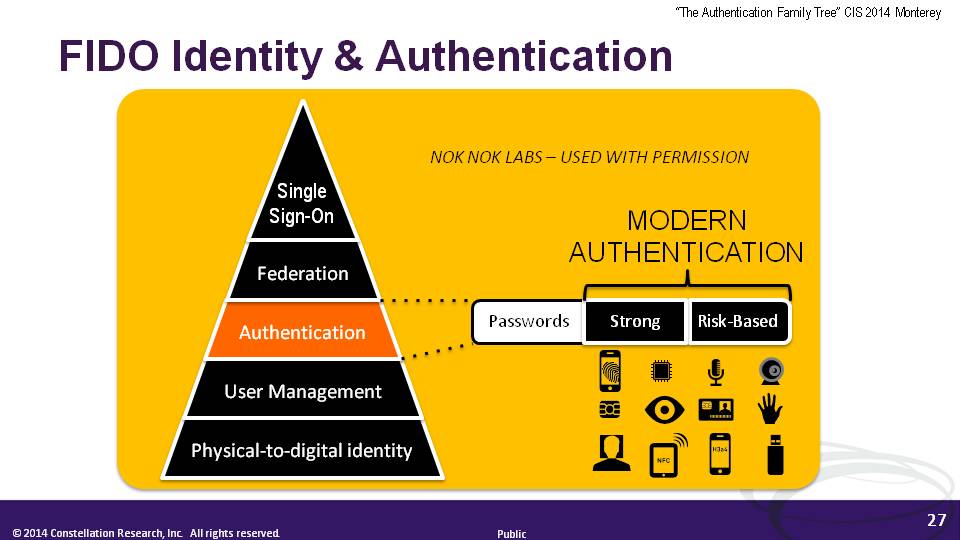
But as a researcher and analyst, the Cloud Identity Summit is where I think you can see the future. People report hearing about things for the first time at a CIS, only to find those things coming true a year or two later. It's because there are so many influencers here.
Last year one example was the Attributes Push. This year, the onus on Attributes has become entirely mainstream. For example, the NSTIC pilot partner ID.me (a startup business focused on improving veterans' access to online discounts through improved verification of entitlements) talks proudly of their ability to convey attributes and reduce the exposure of identity. And Paul Grassi proposes much more focus on Attributes from 2015.
Another example is the "Authorization Agent" (AZA) proposed for SSO in mobile platforms, which was brand new when Paul Madsen presented it at CIS Napa in 2013. Twelve months on, AZA has broadened into the Native Apps (NAPPS) OpenID Working Group.
Then there are the things that are nearly completely normalised. Take mobile devices. They figured in just about every CISmcc presentation, but were rarely called out. Mobile is simply the way things are now.
But there was a lot of explicit mention of hardware. I've already made much of Andre Durand's keynote on tokens. It was the same throughout the event.
- There was a session on hybrid Physical and Logical Access Control Systems (PACS-LACS) featuring the US Government's PIV-I smartcard standard and the major ongoing R&D on that platform sponsored by DHS.
- Companies like SecureKey are devoted to hardware-based keys, increasingly embedded in "street IDs" like driver licenses, and are working with numerous players deep in the SIM and smartcard supply chains.
- The FIDO Alliance is fundamentally about hardware security, leveraging embedded key pairs to attest to the pedigree of authenticator models and the attributes that they transmit on behalf of their verified users. FIDO promises to open up the latent authentication power of many 100s of millions of devices already featuring Secure Elements of one kind or another. That is PKI the way nature intended all along.
- And the good old concept of "What You See Is What You Sign" (WYSIWYS) is making a comeback, with mobile platform players appreciating that users of smartphones need reliable cues in the UX as to the integrity of transaction data served up in their rich operating systems. Clearly some exciting R&D lies ahead.
MyPOV in closing: Cloud Identity Summit is the only not-to-be missed event on the IDAM calendar.
See you again next year (I hope) in Monterey!

