CISO: Thinking creatively about information assets in retail and hospitality
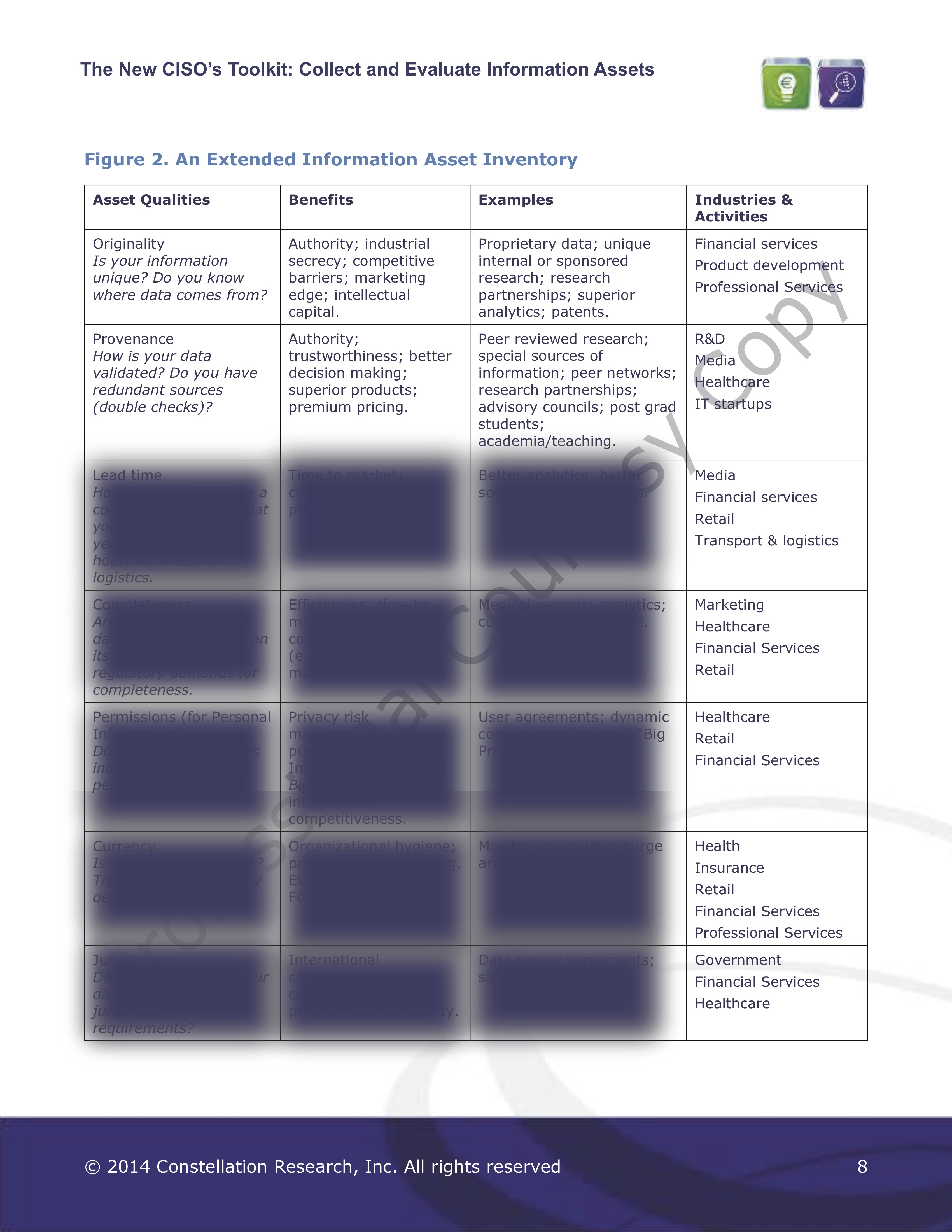
In my last blog Improving the Position of the CISO, I introduced the new research I've done on extending the classic "Confidentiality-Integrity-Availability" (C-I-A) frame for security analysis, to cover all the other qualities of enterprise information assets. The idea is to build a comprehensive account of what it is that makes information valuable in the context of the business, leveraging the traditional tools and skills of the CISO. After all, security professionals are particularly good at looking at context. Instead of restricting themselves to defending information assets against harm, CISOs can be helping to enhance those assets by building up their other competitive attributes.
Let's look at some examples of how this would work, in some classic Big Data applications in retail and hospitality.
Companies in these industries have long been amassing detailed customer databases under the auspices of loyalty programs. Supermarkets have logged our every purchase for many years, so they can for instance put together new deals on our favorite items, from our preferred brands, or from competitors trying to get us to switch brands. Likewise, hotels track when we stay and what we do, so they can personalise our experience, tailor new packages for us, and try to cross-sell services they predict we'll find attractive. Behind the scenes, the data is also used for operations to plan demand, fine tune their logistics and so on.
Big Data techniques amplify the value of information assets enormously, but they can take us into complicated territory. Consider for example the potential for loyalty information to be parlayed into insurance and other financial services products. Supermarkets find they now have access to a range of significant indicators of health & lifestyle risk factors which are hugely valuable in insurance calculations ... if only the data is permitted to be re-purposed like that.
The question is, what is it about the customer database of a given store or hotel that gives it an edge over its competitors? There many more attributes to think creatively about beyond C-I-A!
Utility
- It's important to rigorously check that the raw data, the metadata and any derived analytics can actually be put to different business purposes.
- Are data formats well-specified, and technically and semantically interoperable?
- What would it cost to improve interoperability as needed?
- Is the data physically available to your other business systems?
- Does the rest of the business know what's in the data sets?
Completeness
- Do you know more about your customers than your competitors do?
- Do you supplement and enrich raw customer behaviours with questionaires, or linked data?
- How far back in time do the records go?
- Do you understand the reason any major gaps? Do the gaps themselves tell you anything?
- What sort of metadata do you have? For example, do you retain time & location, trend data, changes, origins and so on?
Currency & Accuracy
- Is your data up to date? Remember that accuracy can diminish over time, so the sheer age of a long term database can have a downside.
- What mechanisms are there to keep data up to date?
Permissions & Consent
- Have customers consented to secondary usage of data?
- Is the consent specific, blanket or bundled?
- Might customers be surprised and possibly put off to learn how their loyalty data is utilised?
- Do the terms & conditions of participation in a loyalty program cover what you wish to do with the data?
- Do the Ts&Cs (which might have been agreed to in the past) still align with the latest plans for data usage?
- Are there opportunities to refresh the Ts&Cs?
- Are there opportunities for customers to negotiate the value you can offer for re-purposing the data?
Compliance
- When businesses derive new insights from data, it is possible that they are synthesising brand new Personal Information, and non-obvious privacy obligations can go along with that. The competitive advantage of Big Data can be squandered if regulations are overlooked, especially in international environments.
- So where is the data held, and where does it flow?
- Are applications for your data compliant with applicable regulations?
- Is health information or similar sensitive Personal Information extracted or synthesised, and do you have specific consent for that?
- Can you meet the Access & Correction obligations in many data protection regulations?
For more detail, my new report, "Strategic Opportunities for the CISO", is available now.


