2015 Event Schedule
2015 Event Schedule
Below is a list of the events I will be attending in 2015.
The information will change frequently, so please check back for the most up to date information.
Below is a list of the events I will be attending in 2015.
The information will change frequently, so please check back for the most up to date information.
 This report is about how Customer Service and Support is evolving into Customer Success Management as top differentiator by companies and brands that understand the importance of the digital disruption and how it is affecting their business and their customers.
This report is about how Customer Service and Support is evolving into Customer Success Management as top differentiator by companies and brands that understand the importance of the digital disruption and how it is affecting their business and their customers.
This is one of Constellation’s reports on the State of Enterprise Technology in which we assess the state of technologies Constellation has identified as essential to digital transformation. This research report explores a key area – customer service and support.
Next-Generation Customer Experience Guides Organizations toward Customer Segments of One
The theme of Next-Generation Customer Experience analyzes how organizations are making the shift from systems of engagement to systems of experience and mass personalization at scale. Traditional viewpoints of the customer via marketing, sales, service and support, and commerce are collapsing. In fact, customers don’t care what department they talk to for marketing, sales, and service. Customers expect an organization to act as one entity and their front office experiences to match other experiences regardless of touch point.
This customer-centric cohesion requires new paradigms in user experience fueled by the backbone of digital business, including social, mobile, cloud, Big Data, and unified communications. Technology provides a catalyst for new experiences as organizations move from selling products and delivering on brand promise via customer experiences which require a change in organizational DNA and leadership from both the top and from the empowered bottom.
Get ready to make the shift as the front office becomes the back office, and marketing, sales, customer service, and loyalty form the basis of the new engagement strategy. Will you be ready for the next generation of customer experience?
You can find a snapshot of the paper here:
@drnatalie
VP and Principal Analyst
Covering Customer Service and Customer Success Management
The ability to speak confidently and deliver a clear, concise and engaging presentation is what every presenter aims for. I had the privilege to share practical tips and techniques at Microsoft Worldwide Partner Conference 2014 on how to develop your public speaking abilities so you can create and confidently deliver compelling speeches and presentations.
In this presentation, you will learn basic principles of public speaking as well as professional techniques for keeping the audience focused on you and your message.
Related Resources:
 Rackspace chose to implement a global online community powered by Zimbra to provide its customers with a central place to share questions, discuss challenges, rate content and provide feedback about Rackspace’s products. This community focuses on scalable delivery of Rackspace’s signature customer service, educating core customers, increasing customer engagement, and sharing Racker knowledge.
Rackspace chose to implement a global online community powered by Zimbra to provide its customers with a central place to share questions, discuss challenges, rate content and provide feedback about Rackspace’s products. This community focuses on scalable delivery of Rackspace’s signature customer service, educating core customers, increasing customer engagement, and sharing Racker knowledge.
This case study examines Ian White’s implementation and deployment of Zimbra. Ian White won the 2014 SuperNova Award in Next Generation Customer Experience for his leadership of this project.
For more information on the paper, you can find it here.
@drnatalie
VP and Principal Analyst, Constellation Research, Covering Customer Service and Online Communities
First of all it is clear that SAP is committed to the space, announcing 500 (incremental?) developers to be dedicated to IoT, not a small change numbers. And it is also good to see that SAP will use the HANA Cloud Platform (HCP), its PaaS product for the effort (more here). So let’s take a look at the first three use cases that SAP wants to tackle:
Next let’s look at the technologies SAP has at its disposal and SAP wants to use in these IoT use cases:
SAP Response - HANA has addressed this concern with Dynamic Tiering, using a columnar disk technology integrated with HANA that supports unstructured data storage and retrieval (and is integrated with the textual capabilities of HANA in-memory). This address the cheaper storage and analysis of unstructured data and is in market with HANA SPS09. In addition, HANA has integrated the Sybase ESP streaming data analytics (CEP) engine into core HANA functionality (HANA Smart Data Streaming), so now lightweight analysis and correlations from streams like sensor data can be accomplished in HANA Smart Data Streaming, and additional data can be passed from Smart Data Streaming to HANA for deeper realtime analysis. With Smart Data Streaming, streams of data (filtered or unfiltered) can be passed to multiple tiers of data for storage and analysis, including SAP HANA, SAP IQ, and Hadoop.
My response - Fair enough to raise that unstructured data analysis can be done on cheaper storage with dynamic tiering, certainly a key feature in HANA SPS 09. But the queries will run separate, not on the same data and need to be combined, which makes the engineering process more complex (something I am sure SAP will take care of) - but may ultimately exclude customers from some insights. Running two separate queries and combining the results may but must not lead to the same result as running one query on the combined data. Material for a separate blog post.
And fair to point out the SAP has used the Sybase ESP / CEP capabilities and added them to the HANA core, always good and great to see re-use of working and proven software. CEP certainly has its space in IoT applications.
In summary SAP certainly brings some interesting and valuable scenarios for IoT in the first wave of offerings. On the technology side SAP also brings some interesting products to the table, but we will have to see how they all will play together and how they can enable the next set of customer use cases in the area of IoT.
Learning more about a vendor’s offering is always valuable and creates a better understanding for the angle the vendor has. In SAP’s situation the angle is the one of the business application vendor with a very fast analytical in memory database. And there are certainly a number of challenging IoT scenarios that require real time capabilities, closely intertwined with business applications. Think off real time manufacturing, mass customization, individualized service and real world traffic situations. Not really SAP’s core competence (so far), but certainly scenarios that command a premium price in the IoT world, something SAP certainly wants (and has to) zero in on.
But if this slice of the IoT market is large enough for SAP in the medium run, is something that remains to be seen. Entering the IoT market with none direct offering for Hadoop style BigData and HDD / SDD based cloud storage excludes SAP from the most common IoT projects we see with customers. But what isn’t possible today – can happen tomorrow. Rest assured we will be watching.
Tech Optimization Data to Decisions Digital Safety, Privacy & Cybersecurity Innovation & Product-led Growth Future of Work New C-Suite Next-Generation Customer Experience SAP SaaS PaaS IaaS Cloud Digital Transformation Disruptive Technology Enterprise IT Enterprise Acceleration Enterprise Software Next Gen Apps IoT Blockchain CRM ERP CCaaS UCaaS Collaboration Enterprise Service Chief Information Officer Chief Technology Officer Chief Information Security Officer Chief Data Officer Chief Executive Officer
Constellation recently published our "State of Enterprise Technology" series of research reports. These reports assess the current state of the enterprise technologies Constellation has deemed significant to digital transformation. These reports also describe the future usage and evolution of these technologies. Constellation will continue to publish reports in our State of Enterprise Technology series throughout Q1.
The State of Collaboration in 2015 is my first contribution to this series of reports. This report is designed to help you set benchmarks and prepare for your collaboration future.
Here's an excerpt from the report:
2014 will be remembered as an inflection point where stand-alone tools began to give way to enterprise software with integrated collaboration features. Constellation defines this as Purposeful Collaboration, where social features are native features of the tools people use to get their jobs done. For 2015, the most significant improvement in these tools will be how they leverage vast amounts of information to help people make more informed decisions. Itâs this intersection of collaboration and analytics that will propel the next level of employee productivity.
You can download the report snapshot and table of contents
Today on National Data Privacy Day, TextPower announces that the company has been granted an important patent for a “text messaging authentication system” that is the basis for the company’s TextKey™ platform. Websites using the TextKey™ platform will offer their users higher security, easier logins and less hassle and save themselves from the most common cause of customer support calls — lost login IDs and passwords. TextKey™ will significantly reduce enterprise or e-commerce website operating costs and inoculate them against the most common forms of hacking: social engineering, password theft, key loggers and phishing schemes.
Unlike commonly available authentication systems TextKey™ users send a simple text message (SMS) from their cell phone to authenticate their identity. Through this one simple text message, multiple factors are authenticated using the patented technology forming a highly secure barrier to hacking. The TextKey™ system also employs a secure connection, completely outside the browser environment, that eliminates man-in-the-middle attacks making it significantly more secure than any other SMS-based two factor authentication technologies. Without physical possession of the authorized cell phone and knowing the user’s personal PIN, identity thieves cannot login to an account using someone else’s credentials.
“What an appropriate day to receive a patent for our authentication technology and announce our one-step secure login product, SnapID™,” said Scott Goldman, CEO of TextPower. “SnapID™, a new product based on our patented TextKey™ platform, eliminates the need for both user IDs and passwords. No more remembering, typing, managing or resetting passwords. No more lists, sticky notes or password managers to handle the dozens of login credentials we all use everyday. To login, users ‘just text it’.”
SnapID™ doesn’t just solve the password problem — it eliminates it and will fundamentally change the way people login to websites, use ATMs, buy pay-per-view movies, checkout at cash registers and any other process that requires identification and authentication. Cell phones have already replaced address books, cameras, calculators, boarding passes, navigation systems, music players and even heart rate monitors. By using them to send a simple text message they can now replace userIDs, passwords, authentication tokens, USB keys and the ubiquitous — and reviled — login box on every website.
A SnapID™-enabled website will have a “Login with SnapID™” button along with the traditional username and password fields. Visitors who have registered for a free SnapID™ account will simply click that button; a one-time password then appears on their computer screen. The visitor sends a plain text message with the one-time password from their registered cell phone (which doesn’t need to be a smart phone) and they are then logged in securely. Logging in takes about as long as it takes to send a text message and is explained in this 2-minute video: https://vimeo.com/107771091
For more information on TextKey™, visit http://www.textkey.com. To register for SnapID™ and check out the demo, visit http://www.snapid.co or text “NoMorePasswords” to 81888.
Next-Generation Customer Experience Digital Safety, Privacy & Cybersecurity Security Zero Trust Chief Customer Officer Chief Information Security Officer Chief Privacy Officer“People trust people, not brand advertising.” For the last few years, marketing analysts and social media marketers have been sharing copious studies and statistics which reiterate that sentiment. They give credit to social media for this new reality and point to the “wisdom of crowds” effect, which references the observation that people tend to believe what the masses say and share on social media, despite personal experiences or empirical evidence to the contrary. If enough people hold this belief, it must be true.
We trust the wisdom of crowds, despite the fact that we neither know the people who rate restaurants on Yelp! nor have personal relationships with many of the social celebrities who boast insane numbers of followers. Similarly, we don’t personally know many of those in our social circles or the online communities we spend so much time in. Yet, we gladly stepped in line, we trusted.
However, with every passing day, it has become more evident that social media has killed consumer trust.
Pre-social media, we called this phenomenon Bandwagonsim. As defined in the Oxford Dictionary of Psychology, the bandwagon effect is a phenomenon whereby the rate of uptake of beliefs, ideas, fads and trends increases the more that they have already been adopted by others. In other words, the bandwagon effect is characterized by the probability of individual adoption increasing with respect to the proportion of people who have already done so. Social media amplifies this effect by allowing more people to become content creators and by facilitating more connections to more people.
It’s often said that “marketers ruin everything” and in this case, I tend to agree. I’m picking on marketers here but in reality, the blame could fall squarely on the lap of most businesses who sought to take advantage of social media. In their efforts to earn free media, brand awareness, “Likes,” mentions, and followers, business have attempted to create short cuts that generate faster results for less time and investment.
Cyber-shilling has become a lucrative business, offering those with cash the opportunity to receive thousands or tens of thousands of positive reviews, fans, followers, and 5-star ratings. Cyber-shilling continues to make news when businesses are sued for posting fake reviews and social networks are called out for not doing enough to prevent them. Forget social proof; social trust is what businesses should be focused on and that trust is eroding, fast.
Klout became popular for using gamification tactics to create and/or encourage social media “influencers.” In turn, the social scoring platform would sell access to these social celebrities in hopes that they would shill for corporate sponsors who shower them with product samples or free services. Klout is essentially a non-player in today’s social influence marketing game but newer players such as HelloSociety, Niche, and TapInfluence are stepping up. Instead of promoting influence scores, they connect businesses with content creators and help them develop and share the content that is more relevant to their audiences. Are consumers fooled?
On a more personal scale, “like-for-like” schemes are constantly in play where enterprising individuals work together to bolster each other’s social profiles in order to appear more popular, relevant, and influential.
All this worked – for a while. Businesses earned a lot of free media and brand awareness; individuals were elevated to social celebrity status. However, it didn’t take the general public long to figure out that cyber-shilling, gamified endorsements, and native advertising were real, and in no time, the inherent trust we placed in our social communities was lost.
The phrase “people trust people, not brand advertising” should be updated to state: “People trust real people and real friends, not social media and/or brand advertising.” Nowhere is this more evident than among the Millennial generation, who for all their good intentions and social-do-goodness, are less trusting of what they read and see in social media.
An October 2014 Student Monitor survey queried college students about the the media through which they learn about products and services. The number one channel by which students preferred to receive product/service information was good old-fashioned word of mouth (48%). Interesting, “ads on the Internet” was second at 39%, well ahead of “information on the Internet” (21%) and “product reviews online” (18%).
In fact, when asked specifically about what most influences their back-to-school purchase decisions, the vast majority of Millennials reported that “friend’s recommendation/one-to-one” was “very influential” (58.3%). Compare that to “friends’ recommendations via social media” which was said to be very influential by only 34.1% of respondents or “Pinterest or other visual social sharing channels,” which was said to be very influential by only 18.9%.
Clearly, the pendulum has swung back to traditional word of mouth and away from “the wisdom of crowds.”
In June of 2013, I wrote that social media has led business astray. For all its promised benefits including faster, more effective access to larger communities, it has forced many marketers down a path that leads to lower business revenue. I speculated that the bigger online communities and our social circles grew, the less influential those communities would be regarding purchase decisions.
There’s no denying that consumers are embracing social networking in greater and greater numbers. And, you cannot deny that social media is a phenomenon that has fundamentally changed the way humans communicate, learn, and live. Yet businesses and marketers may have killed the promise of riches for businesses embracing advocacy or influencer marketing strategies by their very own actions.
Is there no trust left in online recommendations and ratings?
Has social media killed consumer trust?
Sam Fiorella
Feed Your Community, Not Your Ego
The post Social Media Has Killed Consumer Trust appeared first on Sensei Marketing.
Marketing Transformation Digital Safety, Privacy & Cybersecurity Next-Generation Customer Experience Sales Marketing Future of Work Innovation & Product-led Growth New C-Suite B2C CX Marketing B2B Customer Experience EX Employee Experience AI ML Generative AI Analytics Automation Cloud Digital Transformation Disruptive Technology Growth eCommerce Enterprise Software Next Gen Apps Social Customer Service Content Management Collaboration Chief Customer Officer Chief Marketing Officer Chief People Officer Chief Human Resources OfficerIf the digital economy is really the economy, then it's time we moved beyond hoping that we can simply train users to be safe online. Is the real economy only for heros who can protect themselves in the jungle, writing their own code, as if they're carrying their own guns? Or do we as a community build structures and standards and insist on technologies that work for all?
For most people, the World Wide Web experience is still a lot like watching cartoons on TV. The human-machine interface is almost the same. The images and actions are just as synthetic; crucially, nothing in a web browser is real. Almost anything goes -- just as the Roadrunner defies gravity in besting Coyote, there are no laws of physics that temper the way one bit of multimedia leads to the next. Yes, there is a modicum of user feedback in the way we direct some of the action when browsing and e-shopping, but it's quite illusory; for the most part all we're really doing is flicking channels across a billion pages.
It's the suspension of disbelief when browsing that lies at the heart of many of the safety problems we're now seeing. Inevitably we lose our bearings in the totally synthetic World Wide Web. We don't even realise it, we're taken in by a virtual reality, and we become captive to social engineering.
But I don't think it's possible to tackle online safety by merely countering users' credulity. Education is not the silver bullet, because the Internet is really so technologically complex and abstract that it lies beyond the comprehension of most lay people.
Using the Internet 'safely' today requires deep technical skills, comparable to the level of expertise needed to operate an automobile circa 1900. Back then you needed to be able to do all your own mechanics [roughly akin to the mysteries of maintaining anti-virus software], look after the engine [i.e. configure the operating system and firewall], navigate the chaotic emerging road network [there's yet no trusted directory for the Internet, nor any road rules], and even figure out how to fuel the contraption [consumer IT supply chains is about as primitive as the gasoline industry was 100 years ago]. The analogy with the early car industry becomes especially sharp for me when I hear utopian open source proponents argue that writing ones own software is the best way to be safe online. Who changes their own oil anymore? Would most people even know what "change the oil" means? Can you imagine if the warranty on your car required that you change the oil, in the way that Internet banking Ts&Cs require you to keep your computer patched? I wonder what will happen if the time comes that a bank refuses to cover a customer's online fraud losses because their A/V was out of date ...
The Internet is so critical -- and I'd have thought this was needless to say -- that we need ways of working online that don't require us to all be DIY experts.
I wrote a first draft of this blog six years ago, and at that time I called for patience in building digital literacy and sophistication. "It took decades for safe car and road technologies to evolve, and the Internet is still really in its infancy" I said in 2009. But I'm less relaxed about his now, on the brink of the Internet of Things. It's great that the policy makers like the US FTC are calling on connected device makers to build in security and privacy, but I suspect the Internet of Things will require the same degree of activist oversight and regulation as does the auto industry, for the sake of public order and the economy.
Do we as a community have the appetite to temper breakneck "innovation" with proper safety rules?
Digital Safety, Privacy & Cybersecurity Security Zero Trust Chief Information Officer Chief Information Security Officer Chief Privacy OfficerRemember when everything was Intranet focused? It seemed right at that time when all enterprise activity was internal, behind the Firewall, but in reality it was an early development stage in moving to external Internet based activities cumulating in Digital Business. Right now IOT looks to be at the same stage in many enterprises, so it’s the right time to start to understand the bigger picture as well, otherwise todays’ relatively small deployments could be tomorrow’s problem.
Research report now available: The Foundational Elements for the Internet of Things (IoT)
Designing IOT solutions has to, by its very nature, involve networks, but the challenge is that IOT devices are ‘small’ and ‘distributed’, in comparison to conventional networked items such as PCs, Servers, or even Mobility devices. The design of an IoT solution network needs to be approached differently.
The ‘Internet of Everything’ is a Cisco term used to deliberately identify that with the lowering of processor prices, and the rise in ‘consumer’ style devices of all sorts. As demonstrated at Consumer Electronic Show this year, and other trade shows, a huge range of devices are expecting to connect and interact through the Network. The future, which is arriving now, requires not just massively expanded networking capabilities, but a wholly different architecture to cope. An Enterprise might start with an internal deployment of IoT connected to its internal network, as an ‘Intranet of Things’ solution, it will soon as with all Internet based services rapidly expand to embrace external and ‘everything’.
Digital Business means that all Enterprises initial ‘controlled’ Digital Business external activities focusing on sales and purchasing will, as the overall market inevitably changes, will expand. An Enterprise will have to ‘participate’ in the massively connected ‘Internet of Everything’ environment of the Digital Society to gain information, spot opportunities and organize responses.
At the Network level this is part of the fundamental shift already underway. A shift from resource centric (Cloud) based data centers supporting interconnected centralized internal IT networks towards de-centralized networks of small-distributed devices. This introduces a shift in data traffic patterns, as much of the new IOT traffic will remain ‘local’ and with no obvious pattern. This change is fundamental enough to require the network technology architecture to have to change and to need a whole new lexicon of terms.
The diagram below illustrates on the left the usual visualization of a legacy IT network, frequently referred to as ‘tree and branch’ architecture, with the main data flows running to a centralized Data center, or master server. Interconnection with other external Internet resources are, ideally, from the IT security point of view made through well-managed gateways at the Data Centre. The term ‘north-south’ is used to describe the data flows in Tree and Branch architecture which are usually predictable, and manageable.
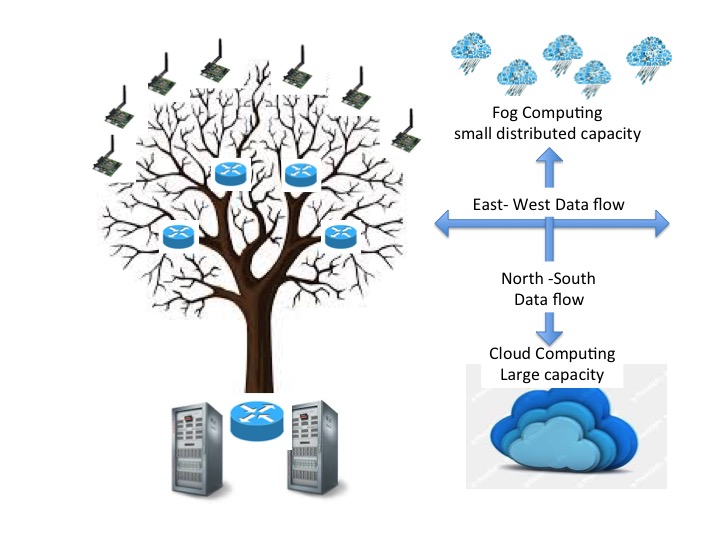
Its difficult diagrammatically to illustrate in such a neat manner the mass connected environment that IoT and Internet of Everything will introduce. The right hand illustration is a simplistic representation mainly to introduce where the various terminologies apply. Here the term North-South continues to describe conventional data flows to and from a centralized set of resources, but introduces the term East-West to describes data flows between the huge number of distributed devices that are networked.
In time East-West (or around the edge) data flows are expected to become dominant as cheap processor power and the sheer number of Devices expected to participate in ‘Smart Sessions’ will out number the more restricted functionality of conventional IT style PCs working in Client-Server Enterprise Applications inside an Enterprise.
The sharp eyed will also have spotted the addition of the term ‘Fog Computing’ to describe the new architecture in which all these IoT, and IoE, smart devices operate creating the East-West data flows. Cloud Computing by contrast supports the architecture that provides large conventional large Data Center resources in the North-South IT architecture.
The term, ‘Fog’, is used by Meteorologists to describe a low level, close to ground, wide spread effect produced by the same conditions that produce Clouds high in the sky. Clouds are generally though of as being more distinctly separate entities whereas Fog swirls round and covers large areas at ground level. As such Fog makes sense as a term to be used for de centralized thin spread computing in contrast to Cloud for the defined centralized computing model. Cisco first introduced the term, but its use has spread, and become increasingly defined as a key part of the architecture required. As an example in the diagram below;
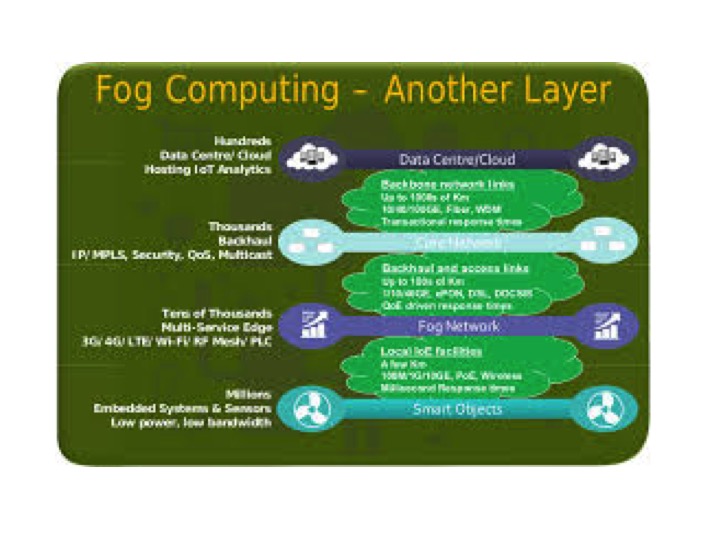
Source; http://thoughtsoncloud.com/2014/08/fog-computing/
IoT is all about Data of course, so how the data environment is made to function is clearly the next question. Cisco also use the term ‘taking the query to the data’ when talking about Fog Computing. This causes more than a little confusion, especially when considering the excellent capabilities of Salesforce and SAP IoT solutions. (Indeed it’s the question of what and how to use the data that defines the differences in the SAP and Salesforce approaches to IoT).
The data from ten IoT devices is easy to handle and use, the data from one hundred devices less so, and the data from a thousand small IoT devices is a flood of small data packets that are extremely difficult to handle. Fog Computing architecture sees local consolidation and processing as one of its main duties.
However, there are three main data flows will usually result in a ‘forward’ of the locally processed data across the network as consolidated data for enterprise processing; 1) a trigger alert condition occurs in the local group; 2) at set times, or intervals, updates are forwarded; or 3) a query is received requesting certain data at that moment.
In IoT solutions, even at the smaller Intranet scale and, without moving to the scaled up adoption of Fog Computing architecture, the whole topic of ‘networking’ data flows is an important consideration. With time, as with the adoption of Client-Server architecture and IP based networking in the past, it will become recognized as a critical success factor in IOT/IoE solutions. Some experienced IoT solution architects even think the Network will function as the new Middleware.
The next post in this series will examine the role of the Network as an Orchestrator of data flows within Virtual networks created by a Query or Event.
The Foundational Elements for the Internet of Things (IoT)
The Elements of Business Architecture for Digital Transformation
Boards Prepare Executives for Digital Business and Digital Leadership